Critical Container Basics
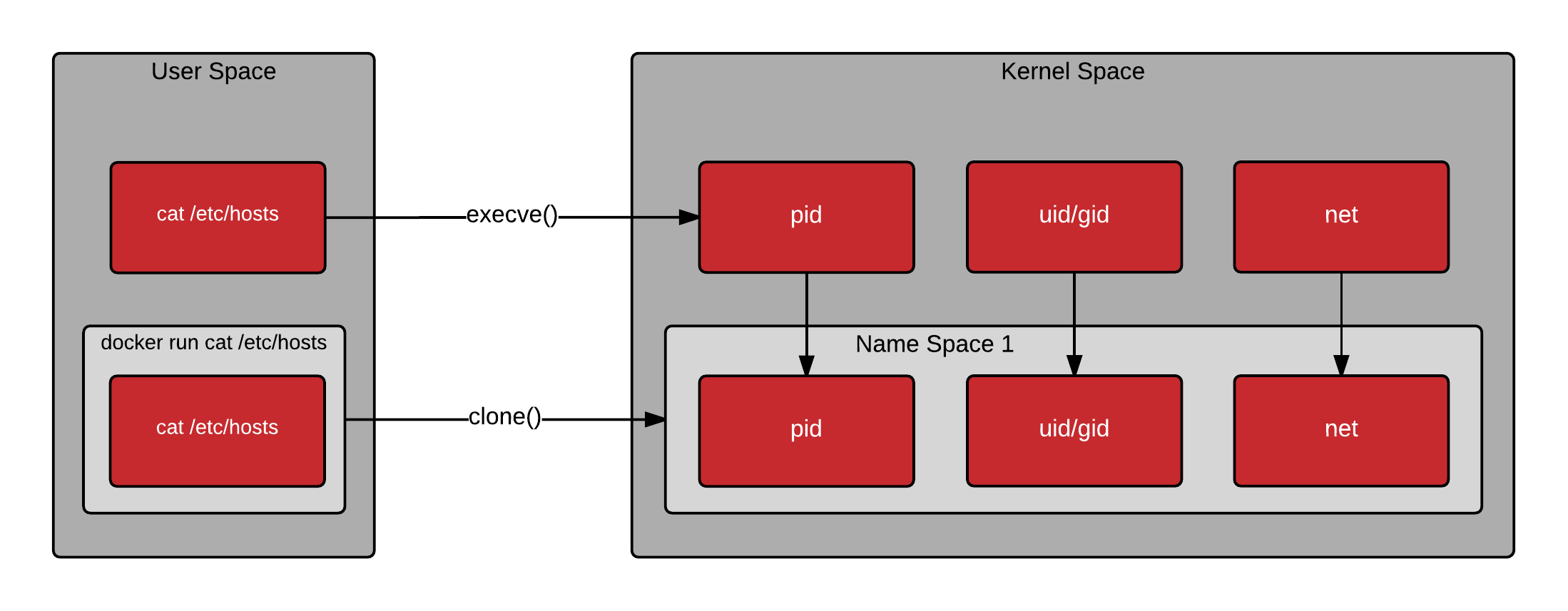
Containers
run inside NAMESPACES.
Below figure summarizes the concept very well.
|
|
Containers are
created by using images. Images are selected
due to TAGS among many image
layers. Image layers occur per build.
Differences between
builds form a layer. Also when building
with a dockerfile, each dockerfile directive create layer for easier
visibility. Each layer has UUID. You can examine layers with Dockviz. You can assign any tag to
each layer.
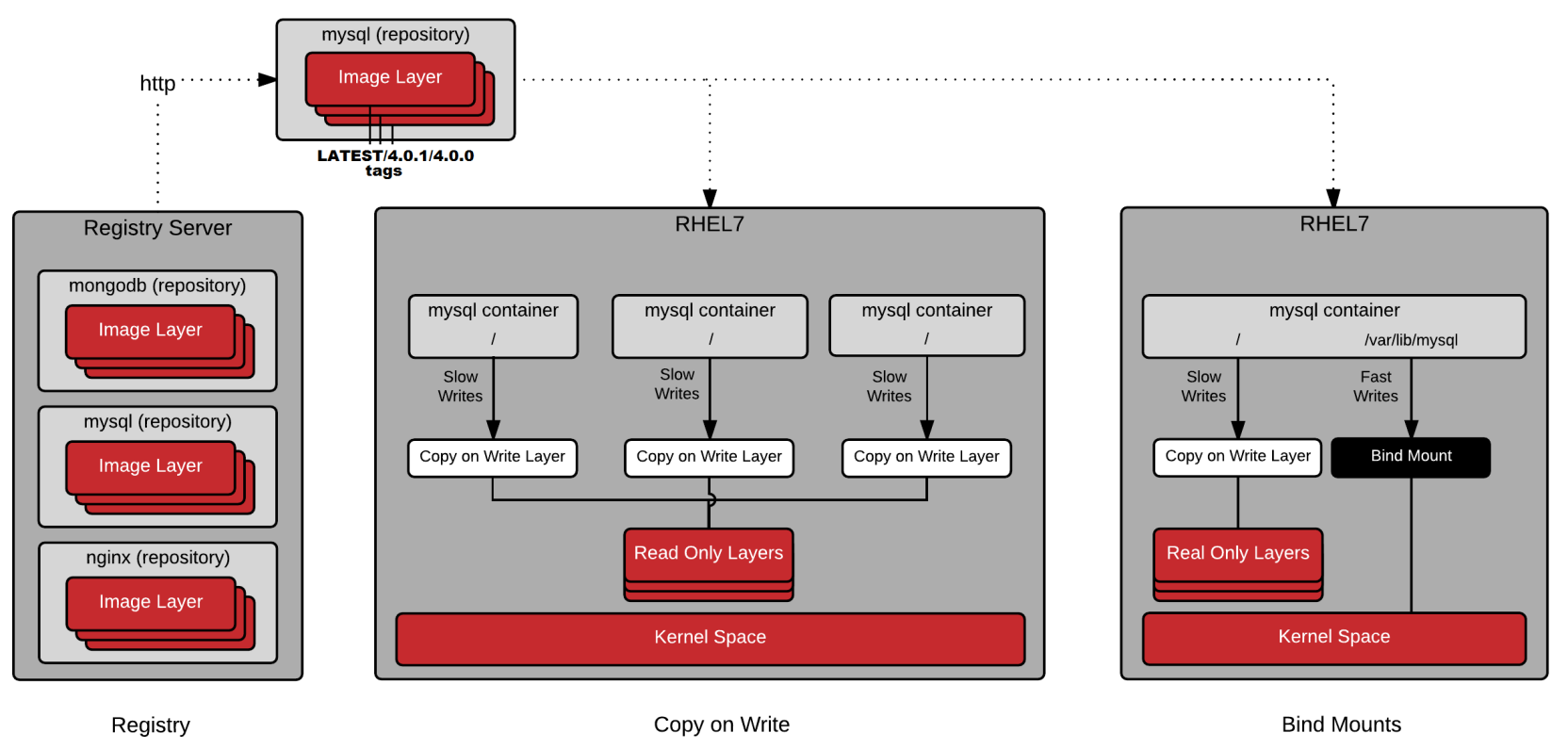
Containers may also have storages
with COW layer or bind mounts.
Below picture details the concept.(both image layers and storage options)
|
|
Some critical
container types are also summarized
as follows:
- containers running "cloud-native applications"
are called "application containers"
- containers running "non-cloud existing applications" are called "pet containers"
- containers running "application" + "virtual
operating system" are called "operating system containers"
"virtual operating
system" = full
INIT cycle to run multiple processes
+ SYSTEMD to install
software
- containers running "with privileges on host kernel" are SPC ( Super Privileged Containers )
E.g: SPC container
can load special kernel module SYSTEMTAP
- container with "system software" that
MUST run before
"container runtime
or orchestration"="System Container"
E.g: ETCD must
be running for OCP.
E.g: You may require a central
SYSLOGD container running
first to gather any kind of log.
Feel free to communicate by bulent.yucesoy@gmail.com